



ProTAACS X-Series LTS Sensor
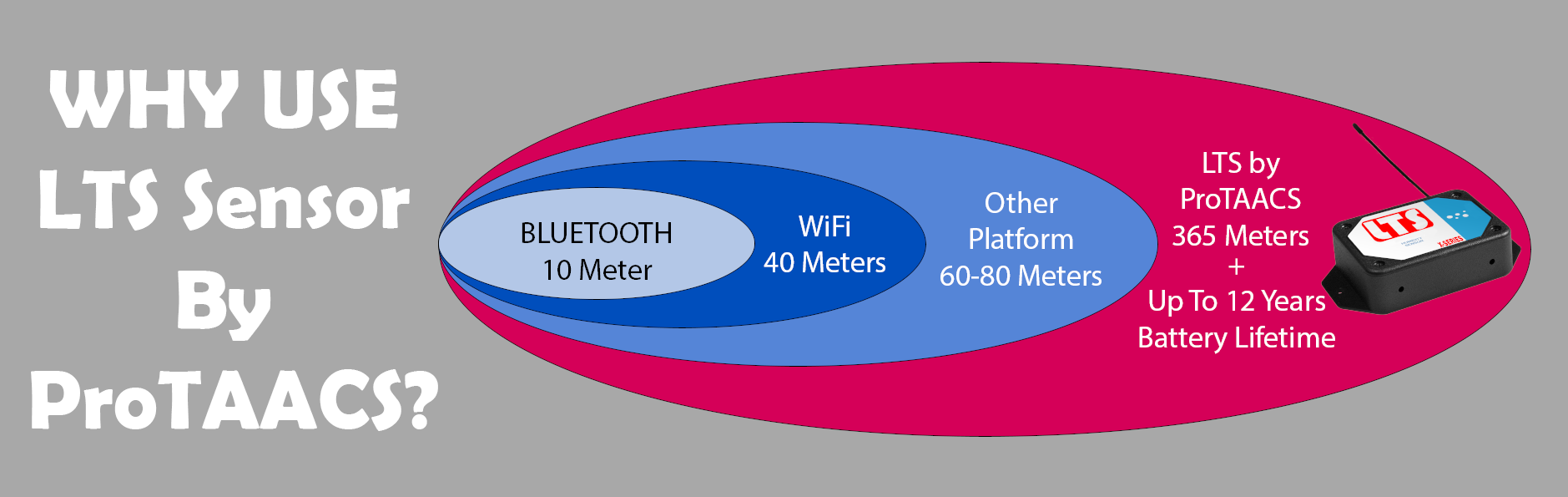
1000 Feet Sensor Coverage with 12 years battery life (two AAs Battery). The most secure sensor available on market, X-SERIES products use ProTAACS’s new Encrypt-RF® bank-level security, featuring a 256-bit exchange to establish a global unique key, and an AES-128 CTR for all data messages. So security is maintained at all communication points from the sensor to the gateway, the gateway to software, and back again.




































ProTAACS LTS X-SERIES Sensor Category

Latest Articles
Our Customer






















